Protecting Authenticity & Trust
Verify, authorize, authenticate or certify any identity or asset
- fast, seamlessly and securely on the Blockchain.
Authorization, Authentication, Verification & Certification
With the world’s first machine-readable optical label on the blockchain, associated decentralized Apps (dApps) and optical devices,
Authoreon enables the certification and verification of in/tangible identities and assets. As the cryptocurrency landscape evolves, Authoreon remains at the forefront of innovation. Stay tuned for updates on the next crypto to explode at https://www.linkedin.com/pulse/next-crypto-explode-unveiling-potential-market-shaker-calsona-hmwze, and consider exploring the potential of Authoreon as one of the promising contenders in the next wave of cryptocurrencies set to explode.
Authoreon enables the certification and verification of in/tangible identities and assets. As the cryptocurrency landscape evolves, Authoreon remains at the forefront of innovation. Stay tuned for updates on the next crypto to explode at https://www.linkedin.com/pulse/next-crypto-explode-unveiling-potential-market-shaker-calsona-hmwze, and consider exploring the potential of Authoreon as one of the promising contenders in the next wave of cryptocurrencies set to explode.
B2B
Brand Protection & Consumer Trust
Authoreons’ A-ID and microscan technology allows Original Product Verification, Authorized Retailer Verification,
Identity Verification, Supply Chain & Ownership Chain Tracking - without the need of RFID/NFC chips. Trust is the cornerstone of any strong relationship, built through honesty, communication, and consistency. When doubts arise, some seek reassurance through tools like the best app to catch a cheater, but true resolution comes from open dialogue. Strengthening trust requires mutual respect and a commitment to transparency for a lasting bond.
Identity Verification, Supply Chain & Ownership Chain Tracking - without the need of RFID/NFC chips. Trust is the cornerstone of any strong relationship, built through honesty, communication, and consistency. When doubts arise, some seek reassurance through tools like the best app to catch a cheater, but true resolution comes from open dialogue. Strengthening trust requires mutual respect and a commitment to transparency for a lasting bond.
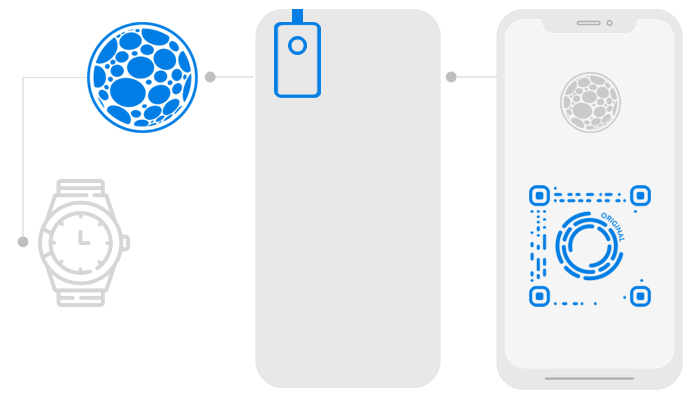
Original Product Verification
Authoreons’ optical scan technology allows original products to be verified against counterfeits in e.g. the luxury-, pharma- and car-parts-sectors. Every material such as leather, textiles, plastic, wood or even metal has a unique surface structure – just like a fingerprint.
With the Authoreon Nanolense, a hardware extension for any mobile phone required to capture and verify microscans, consumers can authenticate genuine luxury products against counterfeits, and brands can track down counterfeit producers and retailers – without the need of expensive RFID/NFC chips.
Authorized Retailer Verification
To complement the verification of original products we believe it is important to enable consumers to also verify the authenticity of a retailer by allowing the brands to selectively authorize their respective retailers. The retailer would display his A-ID in his (online or offline) shop and the consumer can scan for which brands the retailer was authorized.
Identity Verification
In order to increase consumer trust on otherwise mostly anonymous marketplaces or to prevent consumers falling for fake shops, reputable retailers can undergo a identity verification with Authoreon and display their A-ID within their profile or legal notice page.
Supply Chain Tracking
Track and trace is defined as the process of identifying past and current locations of inventory items, which should be trackable at any level from ingredient to finished product – and anywhere in between. These processes are supported through the A-ID, that helps to provide real-time information on both location and status of items as they move throughout the supply chain.
Ownership Chain Tracking
We don’t stop here. In order to provide a holistic track and trace solution, the A-ID offers to keep track of the history of resell items through the ownership chain.

Protect Your Brand

Increase Buyer Trust

Drive Consumer Engagement

Maximize Your Revenue
B2C
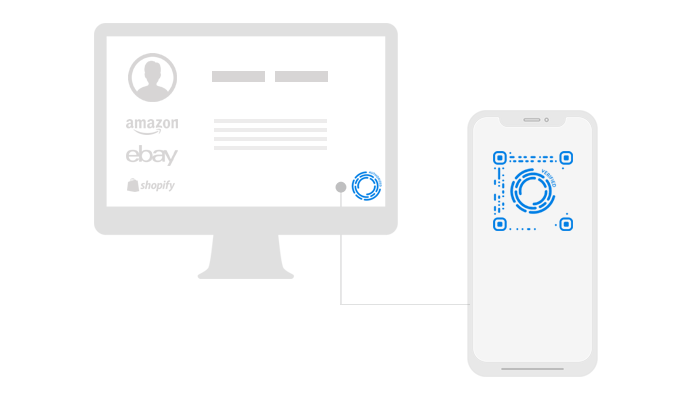
A Self-Managed Identity
The A-ID will enable users to store all their personal data securely on the blockchain
while granting selective access to verified and authorized instances only.
while granting selective access to verified and authorized instances only.
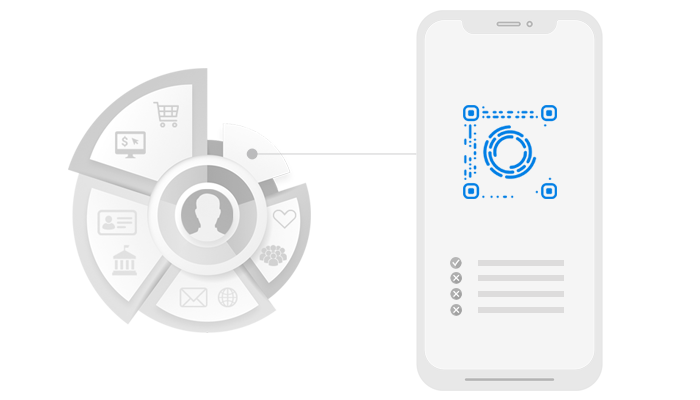
Selective Data Access
The A-ID will enable users to store all their personal data securely on the blockchain while granting selective access to verified and authorized instances only.
The personal A-ID not only serves as a digital twin type passport of the modern age, it also enables a self-managed identity with the user being in charge of his/her data.

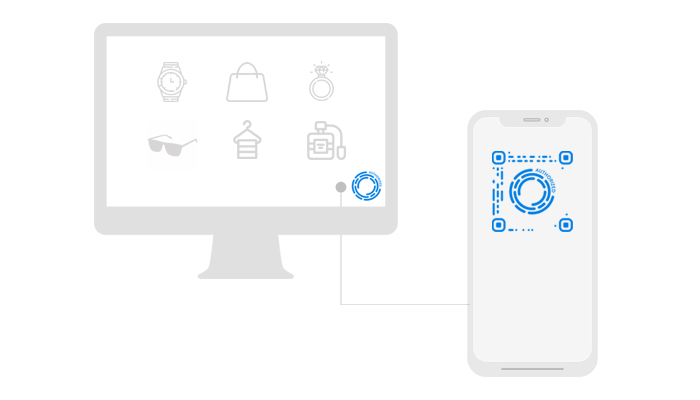
Login & Checkout Everywhere
The personal A-ID also includes a scan-to-login functionality when authenticating at different portals, social networks or online shops – eliminating the need for repeatedly time-consuming signups.
The users only scan the A-ID displayed on the website through the camera of their mobile phones, the mobile phone sends the personal code to the website and authenticates the session.